Trend Micro's security experts have found that attackers have begun using the Angler Phishing Attack Toolkit to find and infect POS systems.
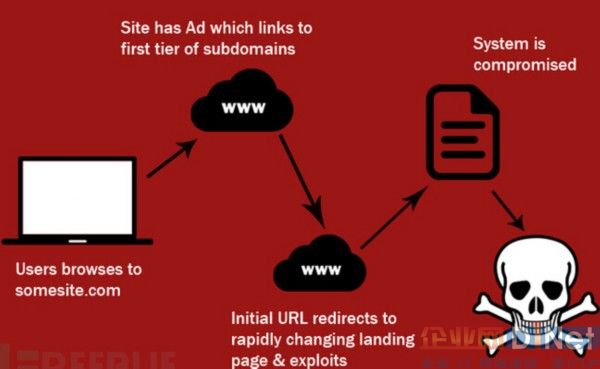
Angler EK Phishing Attack Kit
The Angler EK Phishing Attack Kit was only available in 2013. In just two years, it became one of the most commonly used EKs for field use.
Angler EK is highly confusing, reconnaissance features (which include code to try to detect anti-virus software and virtual machines), anti-reconnaissance (which encrypts the network-transmitted Payload to bypass IDS/IPS detection, using Fileless) "Infections" and other technologies to try to avoid the detection of anti-virus software), and its use of the latest vulnerabilities is updated quickly, even in the use of "0 day" utilization code. As a result, Angler EK is considered by some security researchers to be the most advanced EK in the world.
Sword refers to the PoS system
Security researcher Anthony Joe Melgarejo explained that hackers and cybercriminals are using the popular Angler toolkit to lock PoS systems in complex attacks, a novel use in the cybercrime ecosystem. This is the first time investigators have discovered that hackers use the elaborate Angler toolkit to invade the PoS system platform.
Melgarejo said in a blog post:
"Recently we have discovered a malicious activity that uses the Angler toolbox to infect a PoS system. The attacker uses the Angler toolkit to push a PoS detection Trojan, which is identified as TROJ_RECOLOAD.A, which detects environmental conditions in infected systems. To determine if it is a pos machine or part of a PoS network. It then continues to download specific malware based on the operating environment. We also found that this approach uses the fileless installation feature of the Angler toolkit to evade detection. â€
Attack principle
Melgarejo explained that the Angler toolbox often uses malicious advertising campaigns and often invades websites as a starting point for infection. The infection chain exploited two Adobe Flash vulnerabilities (CVE-2015-0336 and CVE-2015-3104) for specific attacks on PoS systems. Once these vulnerabilities are triggered, the TROJ_RECOLOAD.A malware will invade the target.
The anti-reconnaissance efficiency of the Angler toolbox variant is extremely high, such as in Wireshark network analysis, virtual environments, and sandboxes, which are automatically turned off to evade detection.
Chroma Key Green Screen,Retractable Green Screen,Mountable Green Screen,Green Screen Background
Dongguan Aoxing Audio Visual Equipment CO.,Ltd , https://www.aoxing-whiteboard.com